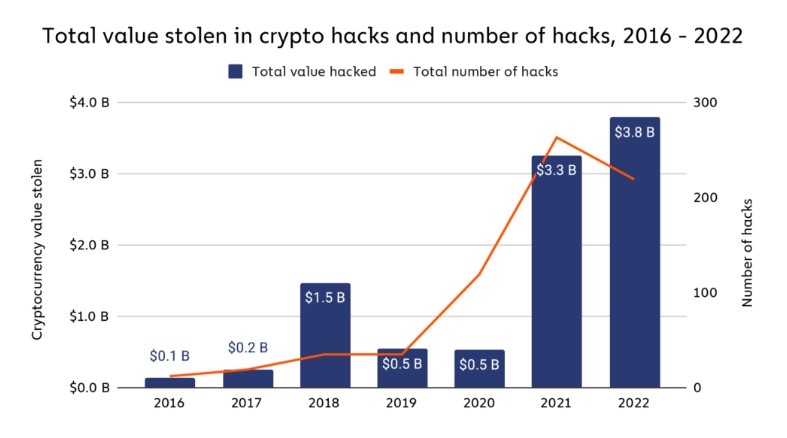
The amount of hacking activity fluctuated throughout the year, with notable peaks in March and October. The latter month saw the highest number of cryptocurrency hacks ever, with $775.7 million being taken in 32 distinct attacks, making it the largest month ever.
In the part that follows, we'll look at which platforms were most frequently compromised as well as how North Korean-affiliated hackers were largely responsible for 2022's cryptocurrency hacking activities.
Hacks of cryptocurrencies frequently target DeFi protocols
Decentralized finance (DeFi) protocols became the main target of crypto hackers in 2021, according to reports on cryptocurrency crime from the previous year. In 2022, this pattern persisted.
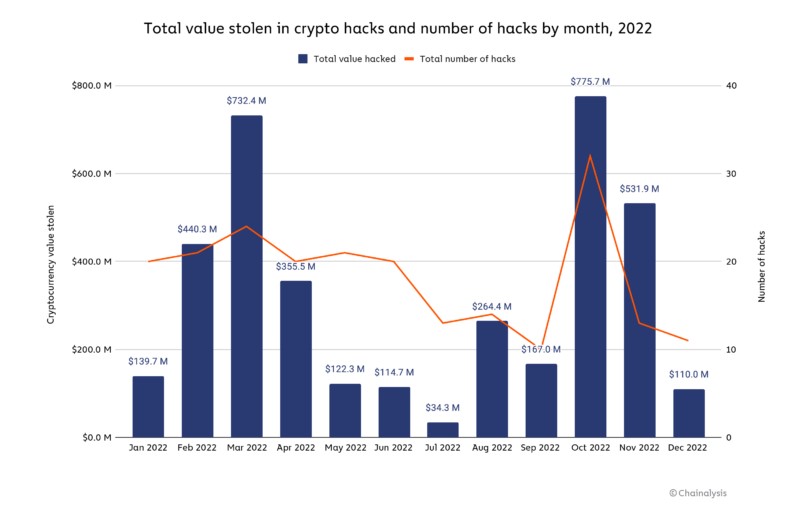
DeFi protocols were the main targets of bitcoin theft in 2021, accounting for 82.1% of all thefts, or $3.1 billion, a significant rise from the 73.3% reported in 2020. And perhaps more concerningly, 64% of the total was stolen using only cross-chain bridges. These protocols make it possible for users to move their cryptocurrency between blockchains, generally using smart contracts that keep the funds supporting the assets transferred to the new chain. This makes them very appealing targets for bad actors. So, once a bridge gathers enough traction, it won't be long before thieves find and exploit its security holes.
How can we make DeFi a safer technology?
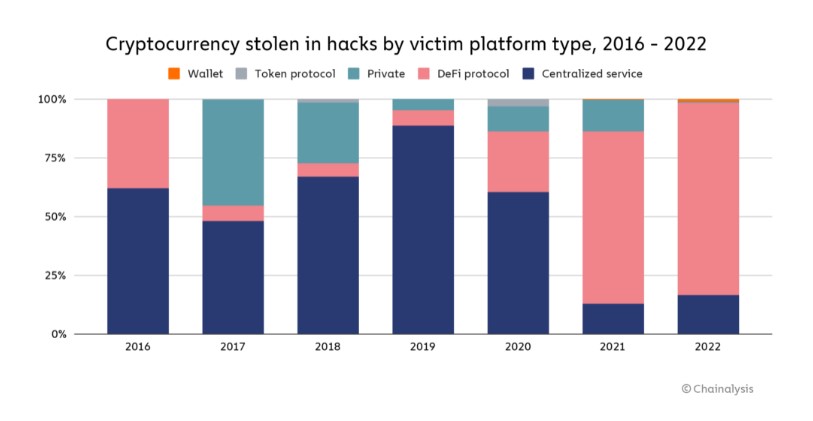
Given its transparency, DeFi has swiftly emerged as one of the crypto industry's most alluring features. Users may view all on-chain transactions and regulating smart contracts for free, giving them full transparency into how their money will be used. Transparency is especially desirable in light of the several crypto market collapses in 2022 that were brought on by a lack of knowledge about some centralized institutions. The same characteristic, meanwhile, can make DeFi susceptible to thieves looking for ways to steal money via exposed code.

Code audits by outside suppliers can assist in securing DeFi protocols. A blockchain cybersecurity company with a perfect track record is Halborn; no protocol that has undergone their assessment has ever been compromised. We discussed how DeFi might strengthen its security protocols with David Schwed, COO of Halborn and a former risk and security consultant at BNY Mellon. One of the key concerns, in his opinion, is a lack of investment in this sector. "Protocols should include 10 to 15 people, each with competence in a separate field, dedicated solely to security," he advised. As incentives are put in place to attract more users, it appears that rapid growth over safety is the priority for DeFi. However, Schwed warned that this could lead to issues in the future: "The community aren't asking for greater security - they're drawn towards high yield opportunities, but that's where you may find yourself in trouble later on."
Schwed advises DeFi developers to consult conventional financial institutions for security advice. Although you don't need to proceed as slowly as a bank, you can learn from what it does.
DeFi developers can evaluate how their protocol holds up to the most typical attack vectors on testnets using simulated attacks.
Profit from the transparency of cryptocurrencies. The fact that transactions in Ethereum are accessible in the mempool prior to confirmation is a significant advantage. Schwed encouraged DeFi developers to regularly watch the mempool for strange activity on their smart contracts in order to identify any attacks as soon as feasible.
If any suspicious activity is found, a circuit breaker can interrupt DeFi protocols and stop transactions. According to Schwed, it is preferable to temporarily annoy consumers than to exhaust the entire protocol.
Additionally, Schwand informed us that authorities might establish minimal security requirements for protocol designers to follow in order to make DeFi safer. DeFi protocols will substantially benefit from adopting stronger security, whether achieved through regulation or voluntary adoption, in order for the ecosystem to flourish, thrive, and eventually infiltrate the mainstream, according to the statistics on DeFi attacks.
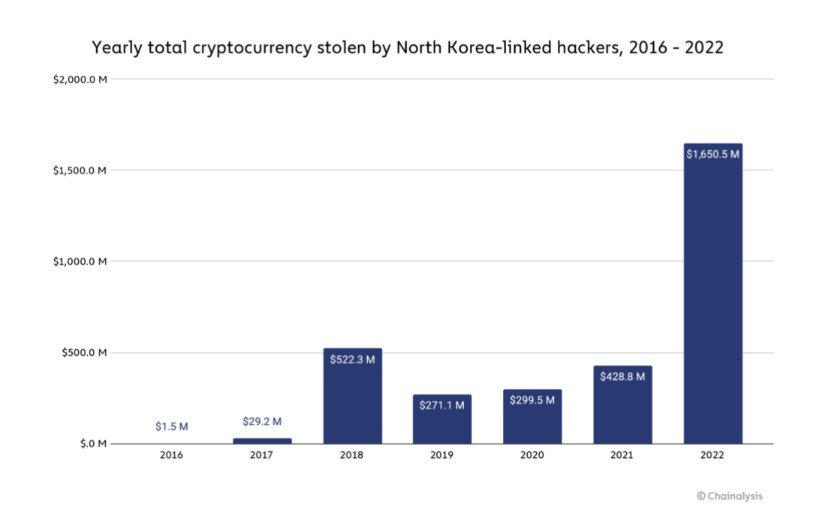
Once more, hackers connected to North Korea steal $1.7 billion.
In recent years, The Lazarus Group, a cybercrime organization associated with North Korea, has been the most active crypto hacker. They obtained over $1.7 billion worth of cryptocurrencies in 2022 alone thanks to various attacks. This is a huge sum that eclipses North Korea's entire exports in 2020, which were only worth $142 million. It is generally acknowledged that the North Korean regime is financing its nuclear weapons projects with these stolen monies.
DeFi methods were used to steal almost $1.1 billion of the money that was stolen globally; North Korea was a big contributor to this trend, which got worse in 2022. As opposed to what one might think given DeFi's qualities that make it more traceable than traditional ones, it has been discovered that North Korean-related hackers frequently move their illicit riches to DeFi services for trading. Instead, this is because such services frequently yield huge sums of cryptocurrency in an unlisted form, which forces hackers to use DEXs to exchange for more liquid assets.
Along with using DeFi protocols, North Korea-affiliated hackers frequently send sizable funds through mixers, which serve as the mainstay of their money-laundering operations. The amount of money transferred to mixers by hackers with ties to North Korea is far more than the amount from hacks carried out by other people or organizations. But what kind of mixers do they employ? Discovered below.
North Korean hackers have shifted to this new mixer as a result of Tornado Cash's OFAC certification.
In 2021 and 2022, hackers with North Korean ties utilized Tornado Cash nearly exclusively to launder cryptocurrency obtained from hacks. For a while, Tornado Cash was the largest mixer in operation, and because of its distinctive technical features, it was challenging to identify the monies it mixed.
When Tornado Cash was approved in August 2022, the hackers modified their approach. Cybercriminals with ties to North Korea are still using Tornado Cash, but they have since started using other mixers, like Sinbad. This might be the case since fewer people are using mixers when less people are using them, which happened after the sanction as Tornado Cash's overall transaction volume dropped. We'll look more closely at why the attackers chose Sinbad as their mixer in the section below.
Those Sinbads
In October 2022, Sinbad, a relatively new custodial bitcoin mixer, started promoting its offerings on BitcoinTalk. We can see from the Chainalysis Reactor graph below that in December 2022, money started flowing into the service from wallets tied to North Korea.
Between December 2022 and January 2023, hackers with ties to North Korea transferred Sinbad 1,429.6 Bitcoin, or almost $24.2 million.
The bitcoin industry is being threatened by hackers with ties to North Korea. When they recovered $30 million worth of bitcoin in the Axie Infinity Ronin Bridge hack in 2020, law enforcement made significant progress. This first-ever seizure demonstrates how the more open blockchain provides authorities with a paper trail years after the fact, which is essential as investigation techniques develop. Such attacks will get tougher and less successful over time as police and security teams become more skilled and OFAC cuts off money laundering services from cryptocurrencies.
Legal, tax, financial, and investment advice are not offered in this content. Before making such choices, the recipients should speak with their own experts. With relation to the use of this material by the Recipient, Chainalysis disclaims all liability and responsibility.
The accuracy, timeliness, suitability, or validity of the material in this report is not guaranteed or warranted by us, and we disclaim all liability for any claims owing to errors, omissions, or other inaccuracies.
Reference: https://blog.chainalysis.com/reports/2022-biggest-year-ever-for-crypto-hacking/
If you have any questions, please don't hesitate to Contact Me.
Back to Blog